Endpoint Edge
A Product Overview of the Byos Secure Endpoint Edge.
The Byos Secure Endpoint Edge


What is it?
- The Byos Secure Endpoint Edge is a small USB device that has a network security stack running on it (protections from OSI Layers 1-5).
- A user plugs it in, authenticates to the device, shuts off their laptop’s native Wi-Fi and connects to the network through the Byos device (running it’s own NAT, DHCP, eDNS, etc.).
- It is plug and play - no software/agent to install on the asset, compatible across Win/Mac/Linux, and identifies as an Ethernet Gadget to the endpoint.
- Overarching application: improved security and control of remote users on public and home Wi-Fi.
What does it do? What problem does it solve?
Protecting corporate and BYOD endpoints from untrusted Wi-Fi networks. It solves the problem of device exposure by providing protection from OSI layers 1 to 5, isolating the connected endpoint onto its own protected microsegment of one within the local Wi-Fi network.
Why was it created? What value does it provide?
The product was created to provide Zero Trust Security at the edge. It does so through microsegmentation, cloaking endpoints from all other devices on the network to remove risk of lateral network infections.
Who is it for?
To be given to traveling and Work From Home employees. Also suitable for high value targets, with highly sensitive IP/data protection (government/defense agents, executives, critical engineers, bankers, etc.)
What industries does it serve?
- Defense/Government
- Manufacturing, Critical Infrastructure
- Food&Beverage, Transportation
- Technology
- Financial Services
- Pharma/Healthcare
What endpoints is it used with?
- Laptops
- Desktops
- Tablets
Technical Requirements and Specifications
- Type of Device: Plug-and-Play USB Ethernet Gateway (RNDIS Gadget).
- Port Requirements: USB-C (USB 3.0/3.1 adapters can be used to connect to a USB-A port).
- Power Draw: Under 2W. The Byos Secure Endpoint Edge is powered solely through its male USB-C connector. A female USB-C receptacle is provided for power pass-through.
- OS Requirements: Any OS compatible with USB-OTG (The product has been tested with Windows, OSX, iOS, and Linux operating systems)
- Driver Requirements: None
- Software Requirements: None. A simple app is provided for Windows and MacOS to make the UX easy.
- Manufactured in: Canada & USA
FAQ
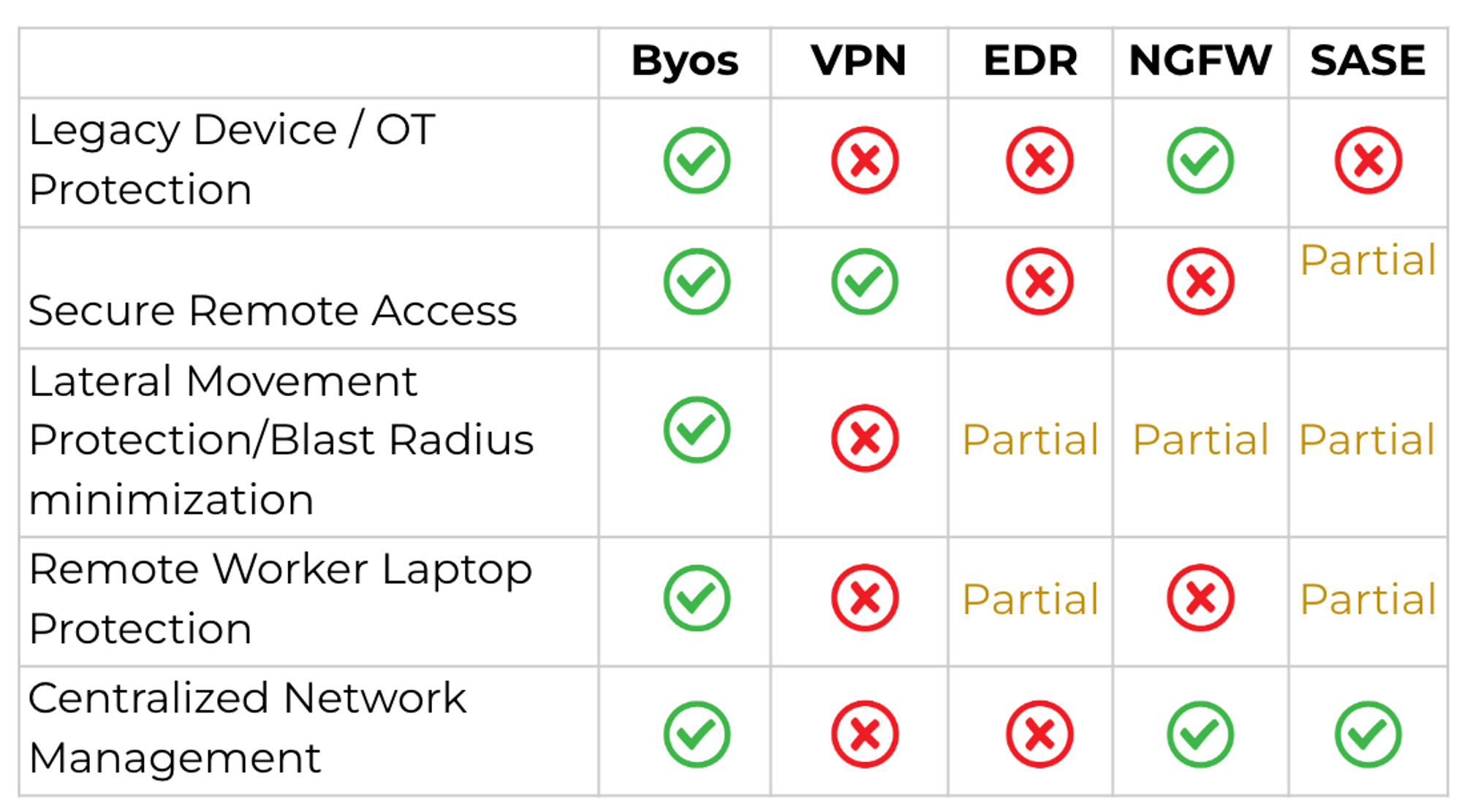
How is Byos different than existing enterprise IT solutions?
Depending on the Use Case, Byos indirectly competes for budget with other types of solutions
- Secure Remote Access Solutions
- Enterprise VPNs or Hardware VPN
- Security-only solutions (ie. Threat Detection, Vulnerability Management)
- EDRs & NGFW
- SASE
How is the Endpoint Edge usage enforced?
- In a managed device environment, the strictest enforcement method is for IT to disable the in-device Wi-Fi antennas of their company-issued devices through a GPO-like policy (MDM or equivalent), to only allow incoming network connections from Byos devices.
- The second method of enforcement is through Byos-Leveraged Identity and Access Management (IAM) conditional authorization - The Byos Endpoint Edge becomes the authoritative signal for whether or not IAM solutions, like Okta, will grant permission to the user to access the desired resource - eg. “Is John Doe using his Byos Endpoint Edge to connect to the Wi-Fi? If yes, he can access Github; if not - access is denied.”
- The least intrusive enforcement policy is for IT to monitor Endpoint Edge usage. The Management Console shows general usage patterns, last login time, and last connected network location, so administrators can understand who’s using their Secure Edge and who’s not.
Will it affect my connection speed or device performance?
- No, the Endpoint Edge does not share computing resources with the endpoint - It doesn't affect the performance of the device. It also does not increase connection latency and the bottleneck in connection speed will always be the network it connects to - providing seamless user experience.
What happens if my users lose their device?
Replacement Endpoint Edge hardware devices can be purchased for $260 USD.
Last updated on November 15, 2023